Release 8.1.5
A67778-01
Library |
Product |
Contents |
Index |
| Oracle8i Parallel Server Concepts and Administration Release 8.1.5 A67778-01 |
|
This chapter explains the role of the Integrated Distributed Lock Manager (IDLM) in controlling access to Oracle Parallel Server (OPS) resources by covering the following topics:
The IDLM component of Oracle8 maintains a list of system resources and provides locking mechanisms to control allocation and modification of Oracle resources. IDLM resources are logical concepts; structures of data. The IDLM does not control access to tables or objects in the database itself. Every process interested in a database resource protected by the IDLM must open a lock on the resource.
OPS uses the IDLM to coordinate concurrent access across multiple instances to resources such as data blocks and rollback segments.
This section explains how the IDLM coordinates resource lock requests by explaining the following topics:
The IDLM coordinates lock requests, ensuring compatibility of resource access rights. In this process the IDLM tracks all lock requests. Requests for available resources are granted and access rights granted are tracked. Requests for resources not currently available are tracked, and access rights are granted when these resources later become available. The IDLM inventories these lock requests and communicates their statuses to users and processes involved.
The IDLM maintains two queues for lock requests:
|
Granted queue |
The IDLM tracks lock requests that have been granted in the granted queue. |
To communicate the status of lock requests, the IDLM uses two types of asynchronous traps (ASTs) or interrupts:
The following figures show how the IDLM handles lock requests.
In Figure 8-1, shared lock request 1 has been granted on the resource to process 1, and shared lock request 2 has been granted to process 2. As mentioned, IDLM tracks the locks in the granted queue. When a request for an exclusive lock is made by process 2, it must wait in the convert queue.
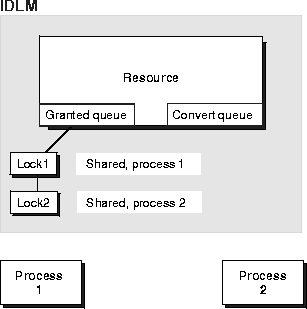
In Figure 8-2, the IDLM sends a blocking AST to Process 1, the owner of the shared lock, notifying it that a request for an exclusive lock is waiting. When the shared lock is relinquished by Process 1, it is converted to a null mode lock or released.
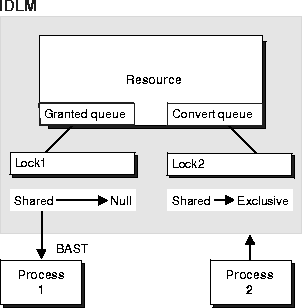
An acquisition AST is then sent to wake up Process 2, the requestor of the exclusive lock. The IDLM grants the exclusive lock and converts it to the granted queue. This is illustrated below in Figure 8-3.
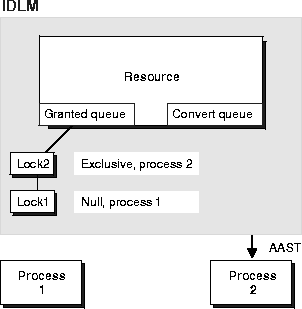
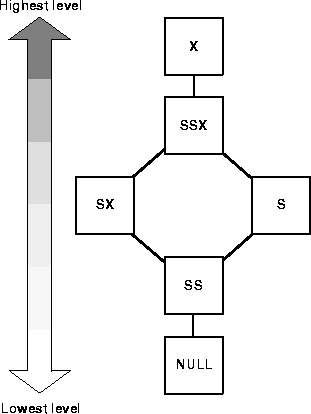
Instances use locks to obtain various rights to a resource. A lock may be initially created on a resource with no access rights granted. Later, a process converts the lock to obtain new access rights.
Figure 8-4 illustrates the levels of access rights or "lock modes" available through the IDLM.
This section describes the following features of the IDLM:
The IDLM maintains a database of resources and locks held on these resources in different modes. This lock database resides in volatile memory and is distributed.
The IDLM has a distributed architecture. In the distributed architecture each node in the cluster (or each OPS instance of an Oracle database) participates in global lock management and manages a piece of the global lock database. The lock database is distributed among all participants. This distributed lock management scheme provides fault tolerance and enhanced runtime performance.
The IDLM is fault tolerant in that it provides continual service and maintains the integrity of the lock database in the event of multiple node and OPS instance failures. A database is accessible as long as at least one OPS instance is active on that database after recovery completes.
Fault tolerance also enables OPS instances to be started and stopped at any time, in any order. However, instance reconfiguration may cause a brief delay.
The IDLM maintains information about locks on all nodes that need access to a particular resource. The IDLM usually nominates one node to manage all relevant information about a resource and its locks. This is node called the "master node".
OPS uses a static hashing lock mastering scheme. This mastering process hashes the resource name to one of the OPS instances that acts as the master for the resource. This results in an even, arbitrary distribution of resources across all available nodes. Every resource is associated with a master node.
The IDLM optimizes the method of lock mastering used in each situation. The method of lock mastering affects system performance during normal runtime activity as well as during instance startup. Performance is optimized when a resource is mastered locally.
When a resource is mastered remotely, all conflicting accesses to this resource result in the transmission of messages to the master node for this resource. This increases internode message traffic and affects system performance.
IDLM performs deadlock detection to all deadlock sensitive locks and resources.
OPS uses the fast and scalable Lamport SCN generation scheme that can generate SCNs in parallel on all instances.
Group-based locking provides dynamic ownership: a single lock can be shared by two or more processes belonging to the same group. Processes in the same group can share and/or touch the lock without opening or converting a new and different lock.
The IDLM provides persistent resources. Resources maintain their state even if all processes or groups holding a lock on it have died abnormally.
The user-level IDLM can normally allocate as many resources as you request; your process size, however, will increase accordingly. This is because you are mapping the shared memory where locks and resources reside into your address space. Thus, the process address space can become very large.
Make sure that the IDLM is configured to support all resources your application requires.
OPS uses two forms of lock ownership:
Group-based locking is an important IDLM feature for Oracle multi-threaded server (MTS) and XA library functionality.
Table 8-2 describes six dynamic performance views you can use to monitor IDLM statistics.
|
See Also:
Please refer to the Oracle8 Reference for a complete description of these dynamic performance views. |