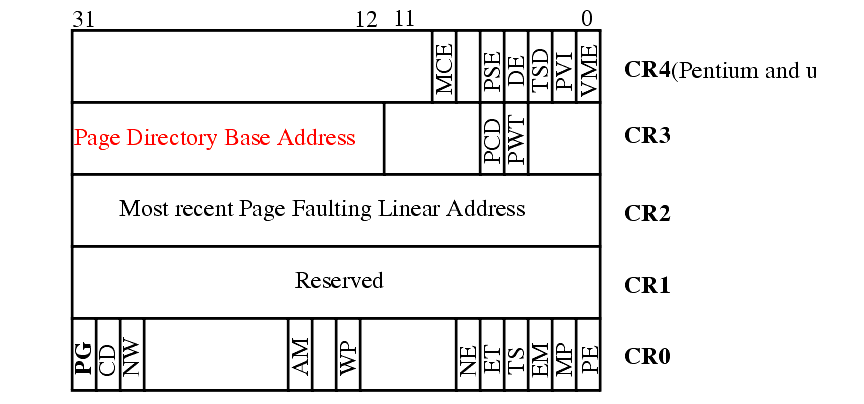
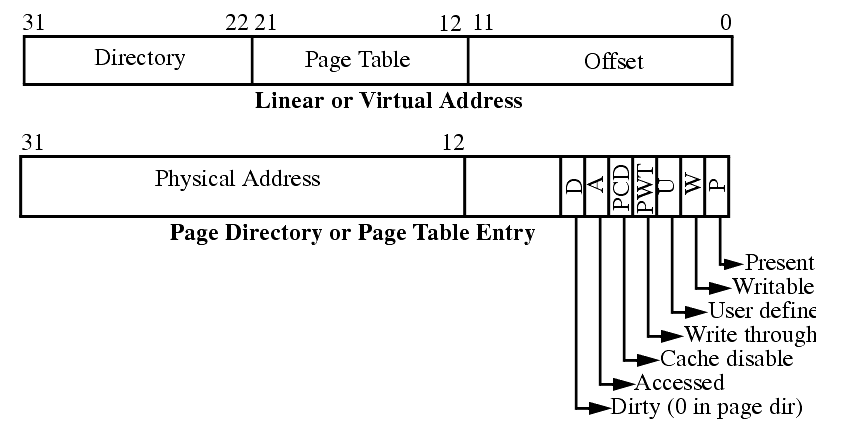
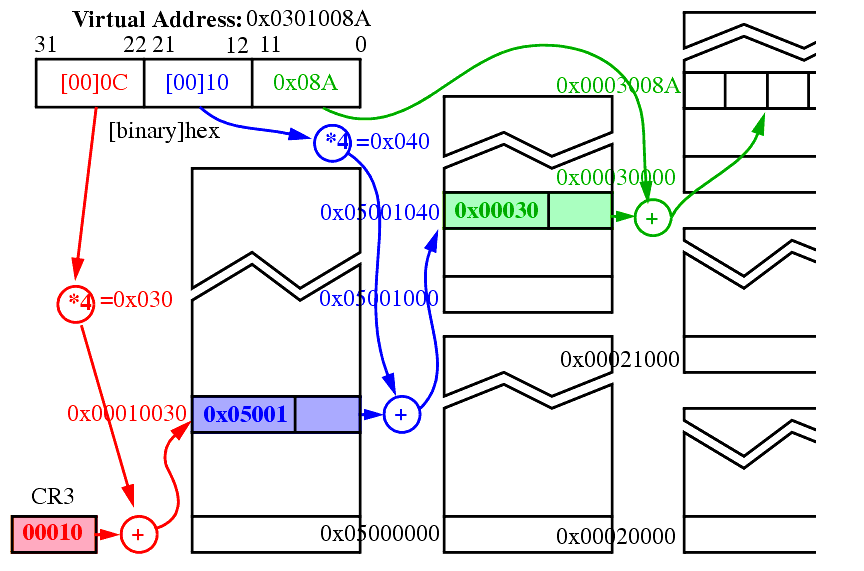
Allows a linear address (virtual address) of a program to be located in any portion of physical memory.
The value in this register is one of the few 'physical' addresses you will ever refer to in a running system.
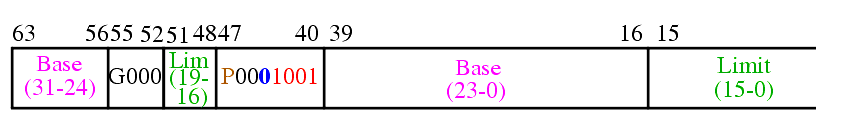
The page directory can reside at any 4K boundary since the low order 12 bits of the address are set to zero.
One to the directory, one to the appropriate page table and (finally) one to the desired data or code item. Ouch!
A Translation Look-aside Buffer (TLB) is used to cache page directory and page table entries to reduce the number of memory references.
The application programmer loads segment register values as before in Real Mode, but the values that he/she puts in them are very different.
Since knowledge of the GDT and LDT is not generally available at compile time, the programmer must use symbolic names.
Instructions such as LDS (load DS), LAR (load access rights), LSL (load segment limit), VERR (verify for read) are available to retrieve descriptor attributes, if the process is privileged enough.
Whenever a segment register is changed, sanity checks are performed before the descriptor is cached.
n Other checks are made depending on the segment type, e.g., data segments, DS cannot be loaded with pointers to execute-only descriptors, ...
m Execute certain instructions, e.g., those that modify the Interrupt flag, alter the segmentation, or affect the protection mechanism require PL 0.
m Reference data other than its own. References to data at higher privilege levels is not permitted.
m Transfer control to code other than its own. CALLs or JMPs to code with a different privilege level (higher or lower) is not permitted.
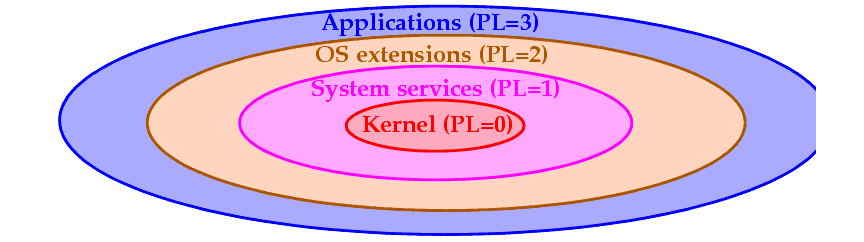
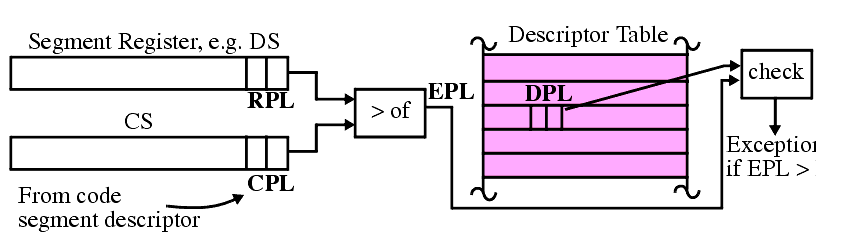
Privilege levels are assigned to segments, as we have seen, using the DPL (Descriptor Privilege Level) field (bits 45 and 46).
When data selectors are loaded, the corresponding data segment's DPL is compared to the larger of your CPL or the selector's RPL.
n Trying to load the DS, ES, FS or GS register with a selector whose DPL is > the DPL of the code segment descriptor generates a general protection fault.
n Trying to use a data descriptor that has the proper privilege level can also be illegal, e.g. trying to write to a read-only segment.
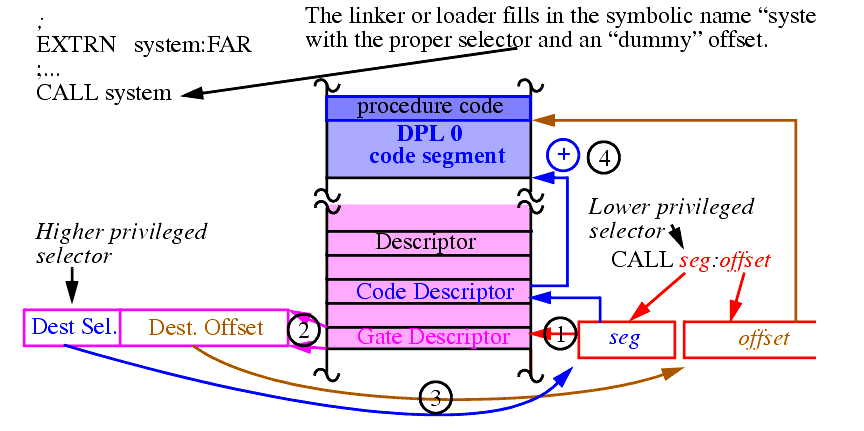
Transferring control to code in another segment is performed using the FAR forms of JMP, CALL and RET.
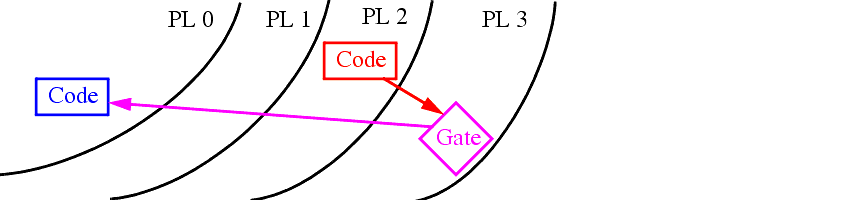
Segments defined this way have no privilege level -- they conform to the level of the calling program.
This mechanism is well suited to handle programs that share code but run at different privilege levels, e.g., shared libraries.
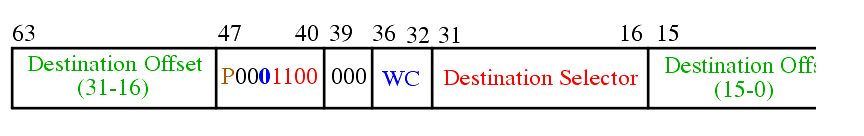
Note, references to call gates are indistinguishable from other FALL CALLs in the program -- a segment and offset are still both given.
Note that both the selector and offset are given in the call gate preventing lower privileged programs from jumping into the middle of higher privileged code.
Call Gates have 'tolls' as well, making some or all of them inaccessible to lower privileged processes.
The rule is that the Call Gate's DPL field (bits 45-46) MUST be >= (lower in privilege) than the process's CPL before the call.