Silence of the labs: Why are we still commuting
the way we did 40 years ago?
Professor Ouri Wolfson
University of Illinois at Chicago
1:00pm Friday 2 December 2011, ITE 227
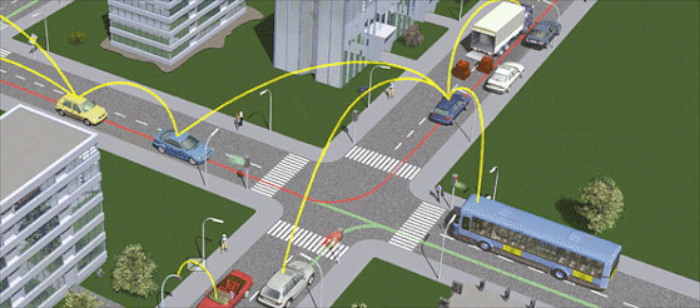
Intelligent Transportation Systems (ITS) have been in research and development since the 70's but their impact so far has been relatively small. In this talk I will argue that this is about to change, and that these systems will soon revolutionize the way we commute. I will describe research issues and Information Technology approaches related to ITS. I will focus on urban transportation, and discuss novel applications enabled by mobile wireless technologies. Such applications have the potential to improve safety, mobility, environmental impact, and energy efficiency of urban transportation. The applications are based on vehicle-to-vehicle and vehicle-to-infrastructure communication, and they epitomize ITS efforts currently undertaken throughout the world, particularly the IntelliDrive initiative of the US Department of Transportation. I will also relate these efforts to our NSF-sponsored IGERT PhD program in Computational Transportation Science.
Ouri Wolfson is the Richard and Loan Hill Professor of Computer Science at the University of Illinois at Chicago, and an Affiliate Professor in the Department of Computer Science at the University of Illinois at Urbana Champaign. He is the sole founder of Mobitrac, a venture-funded high-tech startup that was acquired by Fluensee Co. in 2006.
Ouri Wolfson authored over 180 publications, and holds seven patents. He is a Fellow of the Association of Computing Machinery, a Fellow of the American Association for the Advancement of Science (AAAS), a University of Illinois Scholar for 2009, and serves on the editorial boards of several journals. He co-authored three award winning papers, served as a Distinguished Lecturer for the Association of Computing Machinery during 2001-2003, and participated in numerous conferences as a keynote speaker, general chairman, program committee chairman or member, tutorial presenter, session chairman, and panelist. Most recently he was the keynote speaker at the Mobilware 2010 Conference, and the general chair of the 17th ACM SIGSPATIAL International Conference on Advances in Geographic Information Systems (ACM GIS 2009) . His research has been funded by the National Science Foundation (NSF), Air Force Office of Scientific Research (AFOSR), Defense Advanced Research Projects Agency (DARPA), NATO, US Army, NASA, the New York State Science and Technology Foundation, Hughes Research Laboratories, Informix Co., Accenture Co., and Hitachi Co.
Wolfson’s main research interests are in database systems, distributed systems, and mobile/pervasive computing. Before joining the University of Illinois he has been on the computer science faculty at the Technion, Columbia University, and a Member of Technical Staff at Bell Labs.
Host: Yelena Yesha