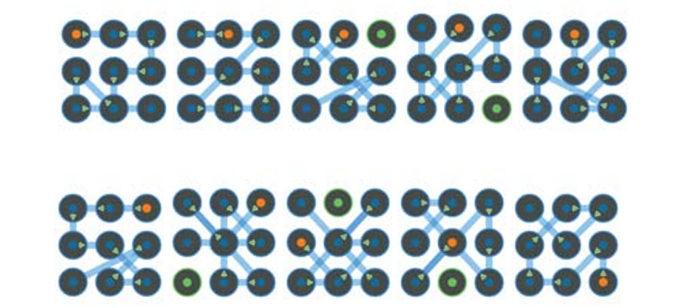
Top 10 highest rated passwords for most “Highly Usable” and “Highly Secure.” The highest rated is in the top left, and moving left-to-right by row, the tenth, highest rated is the lower right.
UMBC Information Systems
Measuring Visual Perceptions of Security
Professor Adam J. Aviv
United States Naval Academy
10:00am – 11:00am Friday, 16 January 2015, ITE 459
This talk presents the results of a user study of the Android graphical password system to measure visual perceptions of security. The survey methodology asked participants to select between carefully selected pairs of patterns indicating either a security or usability preference. By selecting password pairs that isolate a visual feature, a perception of usability and security of different features can be quantified in relatively. We conducted a large IRB-approved survey using pairwise preferences which attracted 384 participants on Amazon Mechanical Turk. Analyzing the results, we find that visual features that can be attributed to complexity indicated a stronger perception of security, while spatial features, such as shifts up/down or left/right are not strong indicators for security or usability.
We extended and applied the survey data by building logistic models to predict perception preferences by training on features used in the survey and other features proposed in related work. The logistic model accurately predicted preferences above 70%, twice the rate of random guessing, and the strongest feature in classification is password distance, the total length of all lines in the pattern, a feature not used in the online survey. This result provides insight into the internal visual calculus of users when comparing choices and selecting visual passwords, and the ultimate goal of this work is to leverage the visual calculus to design systems where inherent perceptions for usability coincides with a known metric of security.
Adam J. Aviv is an Assistant Professor of Computer Science at the United States Naval Academy, receiving his Ph.D. from the University of Pennsylvania under the advisement of Jonathan Smith and Matt Blaze. He has varied research interests including in system and network security, applied cryptography, smartphone security, and more recently in the area of usable security with a focus on mobile devices.